Things about Risk Management Enterprise
Table of ContentsThe 7-Second Trick For Risk Management EnterpriseThe Best Strategy To Use For Risk Management EnterpriseThe Ultimate Guide To Risk Management EnterpriseThe Best Guide To Risk Management EnterpriseThe 8-Minute Rule for Risk Management EnterpriseThe 7-Minute Rule for Risk Management EnterpriseUnknown Facts About Risk Management Enterprise
Right here are a few of its vital attributes that facilities must recognize. Take an appearance. Real-Time Threat Assessments and Reduction in this software application enable organizations to constantly monitor and evaluate threats as they develop. This attribute leverages real-time data and computerized analysis to determine potential risks without delay. Once threats are identified, the software facilitates immediate reduction activities.
KRIs address the trouble of inconsistent or uncertain risk assessment. They address the obstacle of ongoing danger administration by offering tools to check dangers constantly. KRIs improve protection risk oversight, making certain that possible threats are determined and taken care of successfully. The task of risk management ought to not be a difficulty. Companies need to depend on a superior and advanced danger administration software application.
Risk Management Enterprise - Questions
IT risk monitoring is a part of enterprise threat administration (ERM), created to bring IT run the risk of according to an organization's threat cravings. IT risk management (ITRM) encompasses the plans, treatments and technology essential to lower dangers and susceptabilities, while maintaining compliance with relevant regulatory demands. Additionally, ITRM looks for to limit the repercussions of devastating occasions, such as safety and security violations.
While ITRM structures provide valuable advice, it's easy for IT teams to experience from "structure overload." Veronica Rose, ISACA board supervisor and an information systems auditor at Metropol Corp. Ltd., advises using a combination of frameworks to accomplish the very best outcomes. As an example, the ISACA Threat IT structure straightens well with the COBIT 2019 framework, Rose stated.
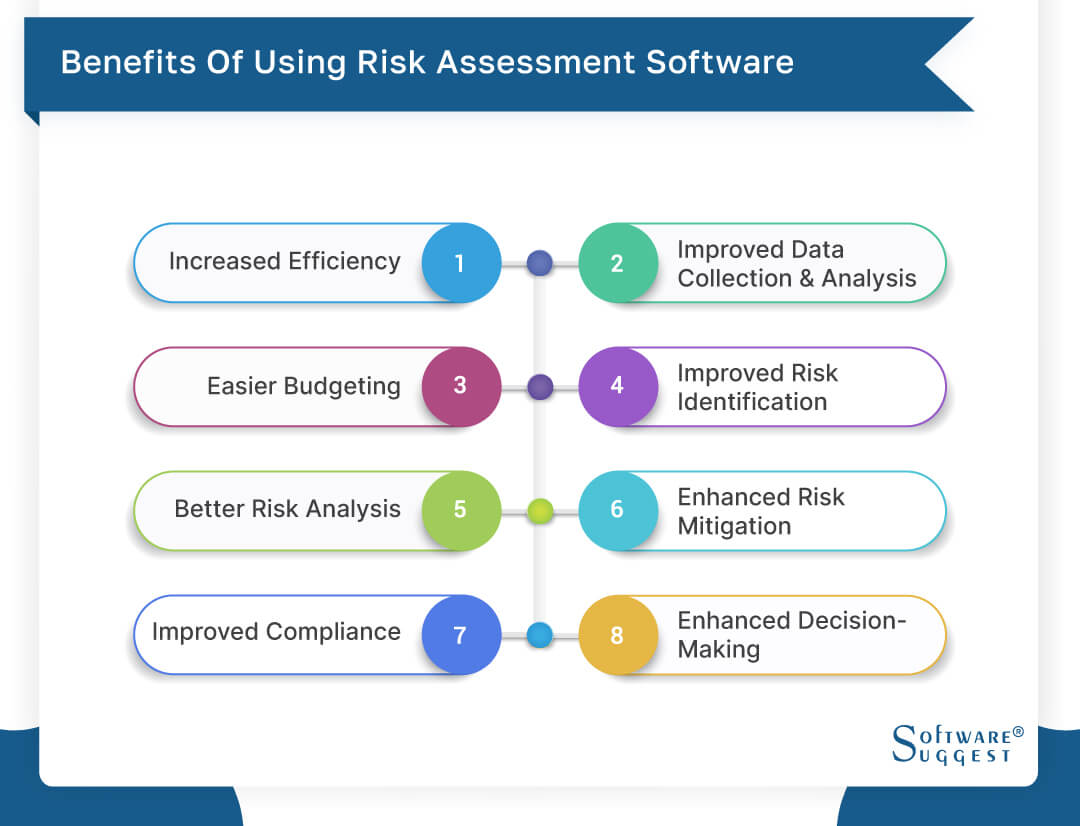
Venture Risk Management Software Program Advancement: Perks & Qualities, Price. With technical advancements, threats are constantly on the surge., services browse with a constantly changing sea of threats.
Getting My Risk Management Enterprise To Work
In this blog site, we will dive into the globe of ERM software program, exploring what it is, its benefits, functions, etc to ensure that you can develop one for your business. Business Danger Monitoring (ERM) software is the application program for planning, routing, arranging, and controlling organization tasks and improving danger administration procedures.
With ERM, companies can make informative decisions to improve the total resilience of business. Read: ERP Application Development Dedicated ERM systems are critical for organizations that on a regular basis manage vast quantities of sensitive information and multiple stakeholders to approve critical choices. Some sectors where ERM has become a conventional system are health care, financing, building and construction, insurance coverage, and info technology (IT).
: It is demanding for any kind of venture to go through an extensive audit. However, it can be avoided by making use of the ERM software program system. This system automates guideline conformity management to maintain the organization secure and certified. Aside from that, it also logs and classifies all the files in the system making it simpler for auditors to review procedures a lot faster.
Indicators on Risk Management Enterprise You Need To Know
You can likewise connect existing software application systems to the ERM using APIs or by adding data manually. Organizations can make use of ERM to evaluate dangers based on their possible impact for much better threat monitoring and mitigation.: Adding this function enables individuals to obtain real-time notifications on their devices about any type of threat that could occur and its influence.
Instead, the software application permits them to set thresholds for different processes and send press alerts in situation of feasible threats.: By incorporating information visualization and reporting in the custom ERM software, companies can obtain clear insights concerning risk trends and performance.: It is mandatory for companies to stick to market conformity and regulatory standards.
These platforms enable companies to apply best-practice risk administration procedures that line up with market criteria, using an effective, technology-driven approach to identifying, evaluating, and mitigating dangers. This blog checks out the benefits of automated threat management devices, the locations of threat monitoring they can automate, and the worth they offer a company.
Risk Management Enterprise Things To Know Before You Buy
Teams can establish types with the pertinent fields and conveniently create various kinds for different threat types. These risk evaluation forms can be distributed for conclusion using automated process that send out notifications to the appropriate staff to complete the kinds online. If types are not completed by the due date, after that chaser emails are instantly sent by the system.
The control surveillance and control testing procedure can also be automated. Firms can make use of automated operations to send out routine control examination notices and personnel can get in the results by means of online types. Controls can additionally be kept an eye on by the software application by establishing rules to send alerts based on control data held in other systems and spreadsheets that is drawn right into the platform via API assimilations.
Danger administration automation software can also support with risk coverage for all degrees of the venture. Leaders can view reports on threat direct exposure and control performance via a range of reporting outcomes including static reports, Power BI interactive records, bowtie evaluation, and Monte Carlo simulations. The capability to pull real time reports at the touch of a button cuts out arduous data manipulation jobs leaving threat teams with more time to analyze the information and recommend the service on the very best strategy.
Organizations operating in affordable, fast-changing markets can't manage delays or ineffectiveness in resolving potential threats. Traditional threat administration making use of hands-on spreadsheet-based processes, while acquainted, commonly lead to fragmented data, lengthy coverage, and a boosted likelihood of human mistake.
How Risk Management Enterprise can Save You Time, Stress, and Money.
This ensures risk registers are always present and lined up with business objectives. Compliance is another critical motorist for automating threat monitoring. Standards like ISO 31000, CPS 230 and COSO all supply advice around threat monitoring ideal practices and control frameworks, and automated risk administration tools are structured to line up with these demands assisting firms to satisfy most generally made use of danger administration criteria.
Seek danger software application systems with an approvals power structure to conveniently establish up process for danger escalation. This capability allows you to customize the sight for every customer, so they just see the data relevant to them. Make sure the ERM software program supplies individual tracking so you can see who entered what information and when.
Go with a cloud-based system to ensure the system gets regular updates from the supplier including new performance. Look for tools that offer task danger monitoring abilities to handle your projects and profiles and the associated threats. The advantages of taking on risk monitoring automation software program expand much past efficiency. Businesses that integrate these options into their ERM method can anticipate a host of tangible and intangible.

The 20-Second Trick For Risk Management Enterprise
While the case for automation is compelling, carrying out a threat monitoring system is not without its obstacles. For one, information top quality is crucial. Automated systems depend on precise, updated info to deliver meaningful understandings. To get over the obstacles of risk monitoring automation, organizations should invest in information cleaning and administration to make certain a solid structure for applying an automated system.
Automation in danger management encourages companies to change their technique to run the risk of and build a more powerful structure for the future (Risk Management Enterprise). The concern is no more whether to automate threat administration, it's exactly how quickly you can begin. To see the Riskonnect in activity,
The solution commonly lies in just how well dangers are anticipated and taken care of. Job monitoring software acts as the navigator in the tumultuous waters of job execution, offering devices that identify and analyze risks and create methods to mitigate them properly. From real-time data analytics to thorough threat monitoring dashboards, these tools offer a 360-degree sight of the project landscape, allowing project supervisors to make enlightened decisions that maintain their jobs on track and within spending plan.